If you think Post-Quantum Cryptography (PQC) is just about making bigger math problems for quantum computers to solve, Simulated Quantum Entanglement (SQE) is here to shatter that illusion. This is not your grandfather’s cryptography.
This article takes a deep dive into SQE’s revolutionary post-quantum encryption, focusing on its mathematical elegance, chemical encryption model, and unbreakable security architecture — all without relying on public-private key cryptography, Quantum Key Distribution (QKD), or any of the usual suspects. If you like mind-bending security concepts, buckle up.
The Problem: Why Most “Quantum-Proof” Encryption is a Temporary Fix
Quantum computing is poised to revolutionize technology, but it also threatens to undermine current cryptographic systems. Shor’s algorithm can break widely used public-key cryptosystems like RSA and ECC making them obsolete, while Grover’s cuts symmetric key strength in half. The cryptographic world has responded with a variety of solutions, each with its own shortcomings:
- NIST Post-Quantum Cryptography (PQC) Algorithms: The National Institute of Standards and Technology (NIST) has been working on standardizing quantum-resistant public-key cryptographic algorithms. These algorithms are based on classical mathematical problems believed to be hard for quantum computers to solve, such as structured lattices, code-based cryptography, multivariate polynomials and hash functions. However, the long-term security of these algorithms remains uncertain, as advancements in quantum computing or new mathematical insights could potentially compromise them. History has shown, “unbreakable” algorithms have a habit of getting broken. Reference: NIST Announces First Four Quantum-Resistant Cryptographic Algorithms
- Quantum Key Distribution (QKD): A darling of the quantum security world, leverages the principles of quantum mechanics to securely distribute encryption keys. However QKD heavily relies on fiber-optic networks or satellites. While theoretically offering unconditional security, QKD faces significant practical challenges, including the need for specialized hardware, high costs, and limitations in transmission distance. Additionally, QKD requires a specialized communication infrastructure and is susceptible to certain types of attacks, such as denial-of-service and man-in-the-middle attacks. Overall it’s insanely expensive and still vulnerable to attacks via quantum repeaters. Reference: The uses and limits of quantum key distribution
- Oversized Key Cryptography: Some approaches suggest increasing key sizes to enhance security (hello, Kyber-1024). I call this the Tim “The Tool Man” Taylor MORE POWER approach. But quantum computers won’t care. Given enough qubits, even a megabyte-sized key is just another snack for a sufficiently advanced quantum computer. Moreover, using excessively large keys can lead to inefficiencies and practical implementation challenges.
- Quantum Random Number Generators (QRNGs): Another approach gaining traction is the use of quantum-generated entropy to produce true random numbers, ensuring unpredictable cryptographic keys. Companies like Qrypt, a vendor utilized by Palo Alto Networks for their QRNG-based API security, offer solutions that enhance key randomness. However, while QRNGs improve unpredictability, they still rely on traditional cryptographic frameworks that quantum computers may eventually compromise.
In summary, while these solutions aim to bolster security in the quantum era, they each have inherent limitations that may render them temporary fixes rather than permanent solutions. SQE’s approach? Throw out public-private key encryption altogether and build something fundamentally unbreakable.
SQE’s Encryption Model: A Self-Evolving, Chemical-Inspired Security System
SQE’s encryption doesn’t function like traditional cryptographic models. Instead, it mimics chemical bonding, where encryption keys behave like molecular structures, constantly evolving in unpredictable ways.
Here’s how it works:
1. No Public-Private Key Exchange
SQE never records, sends, or stores encryption keys. SQE eliminates the concept of static keys entirely. Instead, it dynamically generates evolving digital particles that bind with the data during encryption and unbind upon decryption. These digital particles are unique to each transmission and are never stored, recorded, or exchanged. Only the SQE network of devices (not even the Chief Architect) can recognize and decrypt these newly formed digital particles.
Traditional cryptographic systems rely on static keys that are exchanged, stored, or transmitted — creating attack surfaces vulnerable to theft or quantum decryption. Unlike traditional encryption where even quantum-resistant keys must still be transmitted, SQE’s approach ensures that no static cryptographic artifacts exist — making interception mathematically impossible.
2. Evolving Encryption Digital Particles with Cellular Automata
Before an SQE device (Link or Node) leaves the factory, it undergoes 100,000+ evolutions using cellular automata rules, specifically inspired by Stephen Wolfram’s Rule 30. Rule 30 is a one-dimensional cellular automaton known for producing highly unpredictable yet deterministic patterns from simple initial conditions.
Why Rule 30? This automaton is widely studied in complexity science because it generates chaotic, seemingly random sequences despite being governed by strict rules. It has even been used in random number generators and cryptographic applications due to its inherent unpredictability (Wolfram, 2002).
Application in SQE: Every device in SQE’s ecosystem starts from a single initial seed (1) and undergoes 100,000+ unique evolutions before deployment. Each evolution applies multiple distinct cellular automata rules, resulting in an encryption process that is effectively irreversible.
Mathematically speaking, the probability of reversing these transformations and reconstructing SQE’s evolving digital particles is:
Which is roughly equivalent to winning the Powerball every week from now until the Sun explodes.
(Note: At least I’ll be able to afford that beach house I have always wanted, you know, until the stupid Sun destroys everything)

This number is so astronomically small that it exceeds the total number of atoms in the observable universe, making brute-force attacks infeasible even for a quantum computer. By leveraging cellular automata instead of classical cryptographic key exchanges, SQE ensures that the digital particles evolve dynamically and unpredictably, rendering traditional decryption strategies useless.
3. Every Bit of Data Has Its Own Encryption
In SQE’s world, there’s no single “key” for an encrypted file. Instead, every bit of data has its own unique encryption. SQE’s Chemical inspired encryption refers to the combination of Data and Digital Particles as a Digital Element which is a fully encrypted file, message or really any piece of data stored or transmitted on SQE’s platform.
Data combined with Digital Particles = Digital Element
To decrypt a Digital Element (or message) on the SQE platform, an attacker would have to crack millions of independent encryptions simultaneously, making brute-force attacks astronomically infeasible.
4. The Combination of Data + Digital Particles Change with Every Transmission
In SQE’s encryption model, digital particles evolve dynamically with each transmission which create a mind bending number of Digital Element variations. Even if an attacker were to capture an entire encrypted dataset (good luck), it would be worthless because the encryption state ceases to exist milliseconds after the data is transmitted.
Mathematical Strength: Why SQE’s Encryption is Unbreakable
SQE’s encryption surpasses the entropy of quantum computers themselves. Quantum systems rely on high entropy to maintain security, but SQE’s evolution of Digital Particles generates extreme entropy taking it to a whole new level:
- SQid (1024-bit Unique Identifier): SQE’s SQid is a 1024-bit verifiable signature that represents every entity on SQE’s platform. SQE’s Links can verify the authenticity of all properly formatted SQid by using a mathematical evaluation process that infers the KEY portion of SQid and generates a 256-bit number which is the key to decrypting the entity’s data. There is no mathematical relationship between this KEY and the SQid. SQid is the key component of SQE platform because it is used to create a unique shared key for every task in SQE platform.
- Multi-Layered Digital Signatures: Every transaction in SQE’s blockchain has four layers of encryption:
- A running signature of all involved entities.
- The previous block’s sharded blockchain signature.
- The last reported block signature from the master blockchain.
- The transaction content itself.
Each layer has its own dynamically generated key, making tampering mathematically impossible.
Comparison: SQE vs. Other Post-Quantum Encryption Solutions
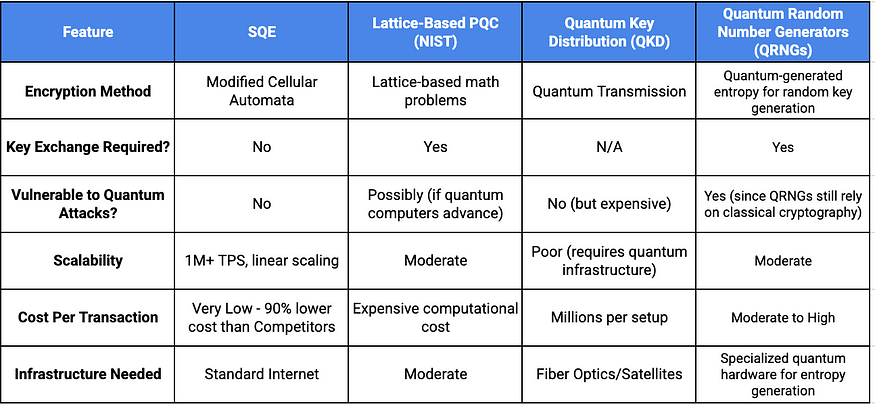
TL;DR: SQE is what happens when you mix theoretical physics with paranoia-level cryptographic security.

Why SQE’s Encryption Model is a Paradigm Shift
To bring all of this together and fully understand why SQE’s chemical inspired encryption model is a complete paradigm shift for the industry you need to understand these three key realities of SQE:
- There’s No Key to Steal: Attackers can’t compromise what doesn’t exist.
- It’s Fully Decentralized: SQE’s approach removes centralized cryptographic authorities. This means no backdoors or centralized authorities with access.
- Even a Quantum Computer Can’t Break It: The time complexity of cracking an SQE-encrypted message exceeds the computational energy of our solar system.
The Future of Post-Quantum Security
For decades, cryptographers have been playing defense against quantum threats by designing increasingly complex math puzzles. SQE rewrites the game entirely by removing the very existence of a static key.
If traditional cryptography is a medieval castle (think stone walls and a moat full of alligators), SQE is an impregnable fortress that exists in a different dimension altogether — one where no siege weapons, quantum or otherwise, can reach (and also includes a moat full of alligators that have lasers).

The post-quantum world is coming faster than we think so I’ll end my post with this question for Cybersecurity Professionals:
Would you rather bet on bigger encryption keys or a system that doesn’t need them at all?
Author: Marz Rock, Follow on Medium





